All UIS enterprise and business applications are in service at this time.
Service Status: Green
20260302 Performance Issue Resolved
All UIS enterprise and business applications are in service at this time.
Service Status: Green
Phishing is a type of online scam where cybercriminals pose as trusted individuals or organizations to steal sensitive information, such as passwords, financial data or university login credentials.
Phishing scams often use urgency or fear to trick you into taking quick action without thinking. These scams are becoming more sophisticated, with some messages now free of obvious spelling errors and even crafted using AI tools.
Look for these red flags when reviewing your emails, texts or messages:
Phishing attempts may also use texts, phone calls or collaboration tools like Teams.
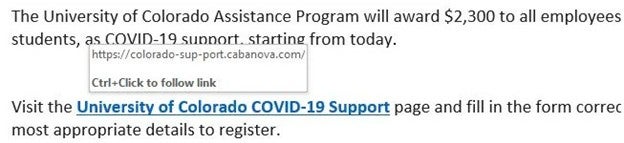
For example, the URL in the image below points to a link that is entirely dissimilar from a normal University of Colorado webpage. Links associated with the university always end with .edu. Also, the “-sup-port-cabanova” wording is not associated with any university service or found in any university URLs. This is clearly a phishing attempt.
1. Don't click any links or open attachments.
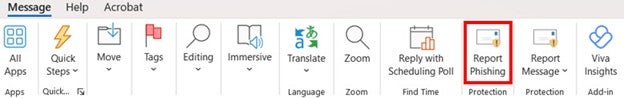
2. Use the Report phishing function in Outlook to send it to the security team.
a. In Outlook, click the Message tab, then select Report phishing.
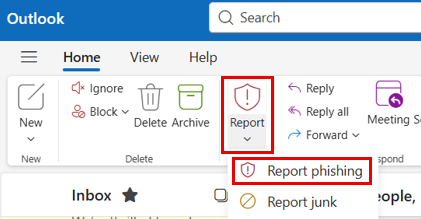
Depending on which version of Outlook you are using, you may need to click Report and select Report phishing from the drop-down menu.
3. If you already clicked a link or entered your credentials:
a. Immediately report it to CU as a possible incident. Visit the Report an Incident and OIS webpage to learn more and find the correct incident report contact.
b. Change your password.
c. Contact the UIS Service Desk for urgent support and guidance.
4. Reporting immediately helps stop cybercriminals, protect others and contain the possible incident. CU does not penalize employees or students for reporting suspicious messages in good faith.
Enable multifactor authentication (MFA) for all university and personal accounts.
Keep your device, browser and applications up to date.
Think before you click: if an email seems urgent, unusual or too good to be true, it probably is. Pause and verify first before proceeding.
Regularly review CU’s Information Security policies and cybersecurity trainings, available on Skillsoft Percipio.
Before acting on a suspicious message, ask yourself:
1800 Grant Street, Suite 200 | Denver, CO 80203 | Campus Mail 050 SYS
CU Help Line: 303-860-HELP (4357), E-mail: help@cu.edu | Fax: 303-860-4301
Add new comment